The Company establishes an information security policy in accordance with the relevant norms of the international standard ISO 27001 and in consideration of the Company's business needs to strengthen information security management, construct the security management and risk management of information assets, and ensure that the confidentiality, integrity and availability of the Company's information assets comply with the requirements of relevant laws and regulations, so that they are protected from internal and external intentional or unexpected threats。
The information security policy shall be reviewed annually in conjunction with the assessment and review of changes in government laws and regulations, environment, business and technology, and its amendments shall be announced and implemented after approval by the Information Security Management Committee。
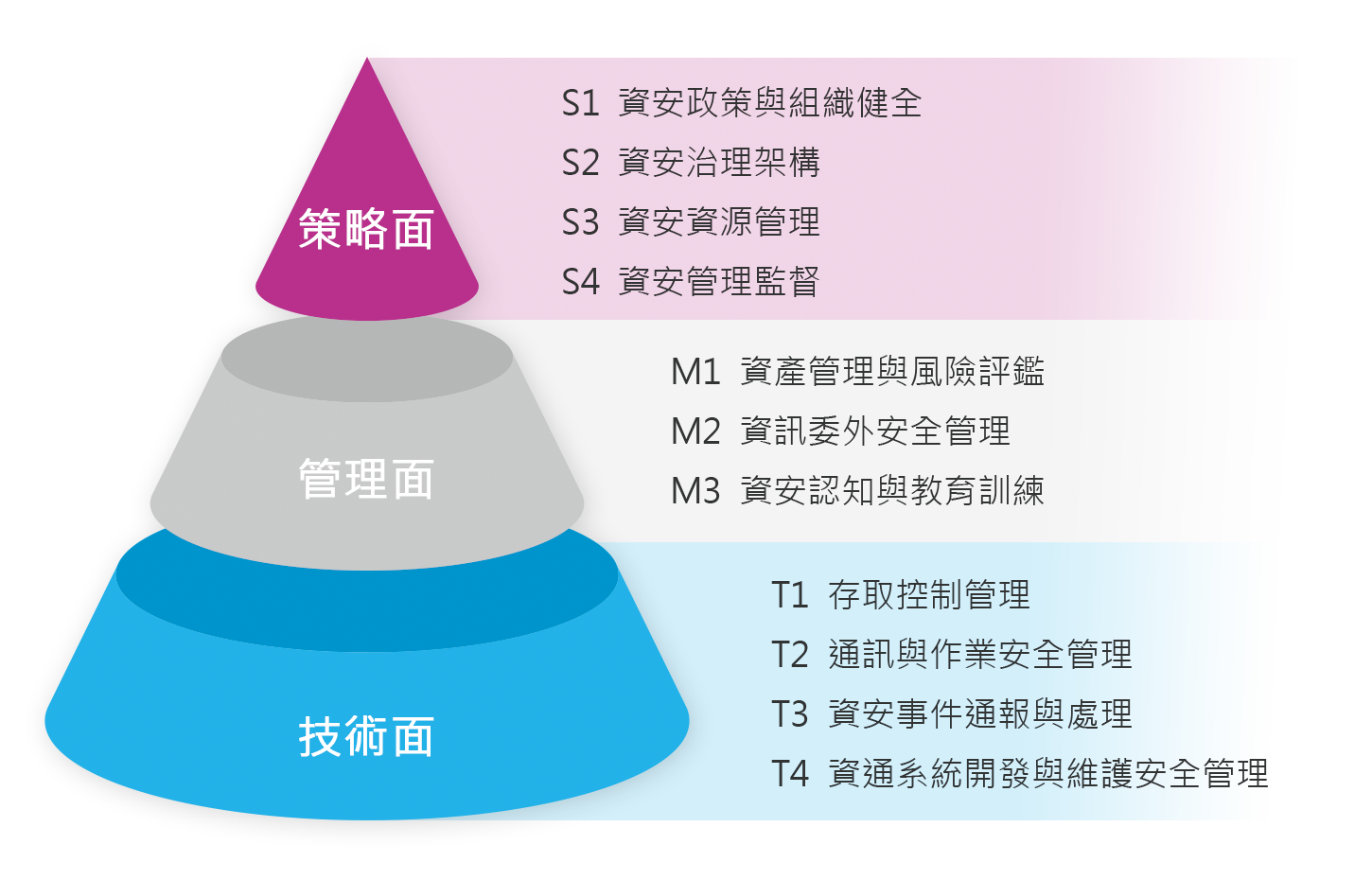
Information security governance architecture
Gudeng uses the information security governance framework as a system to guide and control the information security activities of the organization, with the purpose of ensuring that the information security objectives and strategies undertake the objectives and strategies of the organization's operation, so that information security is consistent with the business objectives, and continuously rewarding the information security governance structure from top to bottom to reduce security risks。
Management:
Management should pay attention to the threats faced by the organization and decide on countermeasures and priorities for existing risks
Business layer:
Critical business and systems should be identified to ensure that the risks of the business are potentially well managed
Maintenance operation layer:
Ensure that critical information assets are fully protected based on management's intent and business criticality
Information Security Policy
As an important supplier of the global semiconductor industry, Jiadeng Precision ensures that the confidentiality, integrity and availability of the company's information assets are protected based on the protection of the company's research and development results, trade secrets, legal provisions and contractual requirements, so as to maintain the company's market competitiveness and protect the interests of customers and partners, and achieve the company's information security management goals。
Information security management objectives
The Information Security Working Group shall review and evaluate the Company's information security management objectives annually, and make amendments to the BSC Group at the annual Strategy Meeting to include them in the annual policy map, and plan and formulate the annual information security management goals in accordance with the provisions of the "MP0006 Policy and Objective Planning Management Procedures"。
Annual security targets:
Strategic main axis: lean production, intelligent manufacturing
- Goal 1: Manufacturers who combine speed and safety in the eyes of customers
- Goal 2: Complete IT systems with traceability
Information security policy and objective review and assessment priorities
- Confidentiality, integrity, availability, and compliance of business (information) services。
- Handling of information security management incidents。
- Information infrastructure, information systems and data backup management。
- Account passcode setting management。
- Management of information safety incidents exposed by the media。
- Management of operational continuity maintenance plan exercises。
- Management of unplanned operational interruptions。
Information security risk management
- When promoting the relevant norms of the information security management system, it is necessary to have a comprehensive and extensive understanding of the company's panorama and the needs and expectations of stakeholders, so as to smoothly define the information security policy。
- Based on the views and consensus of the company's top management on the operational purposes and objectives of the organization, identify the company's mission, core values (values), vision and operational objectives, identify each need and goal of the stakeholders in the core business processes and important work items, analyze the possible impact scenarios and levels when "when the needs and objectives of the stakeholders are not met", in order to decide whether to take appropriate countermeasures or accept risks, and through the risk treatment countermeasures of ISO27001 control clauses To properly analyze and dispose of each identified need and goal, and carry out risk management。
- The Information Security Committee shall also consider the impact that may be caused on the Company if the needs and objectives of the stakeholders are not met, and include the needs and objectives Information Security Management System, hereinafter referred to asISMS)The scope of implementation or verification is set out in the Company's ISMS Declaration of Applicability in accordance with the Company's information security risk management procedures and measures。
Specific management plans for information security
- Prevent external security attacks:Such as threat email statistics, malicious URL prevention。
- Raise the vigilance of staff salaries:Internal phishing letters test staff alertness, internal and external issues and current interviews, and prioritize high-risk projects。
- Prevent internal security threats: such as automatic encryption of archived files, file operation record control, abnormal login analysis of account passwords, access records of external connections, non-authentication devices cannot connect to the intranet, graphical host operation monitoring, and active warning of abnormal host emails。
- Institutional design:Such as the formulation of ISMS management system, regular data backup, off-site backup。